You’re evaluating vendors who will handle your sensitive data: customer records, financial information, tax documents, or employee files. Some vendors have SOC 2 Type I reports and others have SOC 2 Type II.
Does this difference actually matter? Yes.
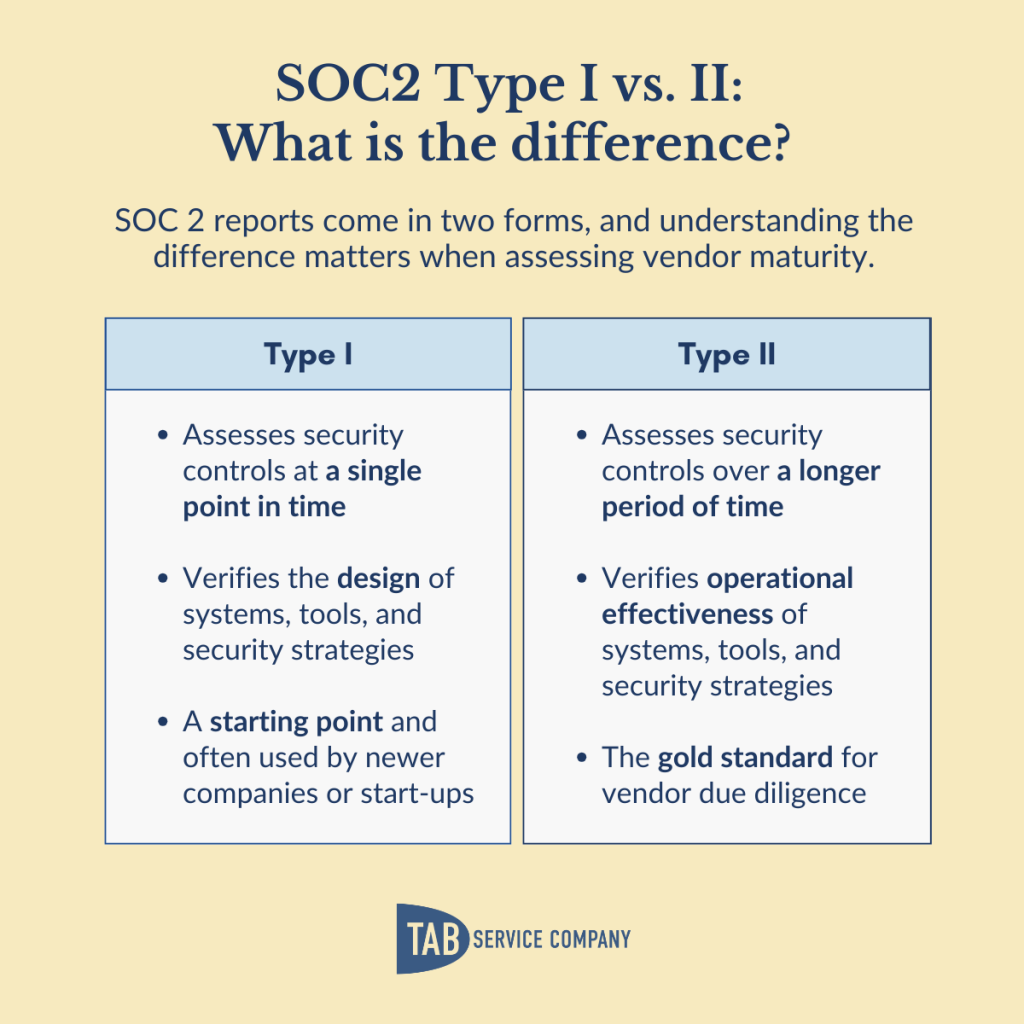
SOC 2 Type II is significantly preferred for vendor selection because it proves controls work consistently over time, not just at one moment. Type I serves as a good starting point for newer vendors building their compliance programs, but Type II provides the level of assurance you need for critical systems and sensitive data.
The Key Difference: Design vs. Proven Performance
SOC 2 Type I: Point-in-Time Assessment
A Type I report checks whether a company’s security controls are designed properly at a single point in time. The auditor reviews policies, procedures, and system descriptions to confirm the controls should work in theory:
- Controls are documented and policies exist
- The security framework is reasonable
- The company understands what controls should be in place
SOC 2 Type II: Operational Effectiveness Over Time
A Type II report checks whether controls are not only designed properly but also working effectively over time (minimum six months but typically a full year).
The auditor goes beyond reviewing documents. They test the controls repeatedly throughout the audit period. Did access controls prevent unauthorized access? Were security incidents logged and handled properly? Were system privileges removed when employees left? The audit aims to provide assurance that:
- Controls work effectively in real operations
- The company maintains controls consistently over 6-12 months
- The security framework operates successfully under actual business conditions
Why SOC 2 Type II Matters for Your Risk Profile
When you trust a vendor with your organization’s sensitive data, you’re extending your security perimeter. How well their security controls work directly affects your risk.
A vendor might show you their Type I report confirming their controls were well-designed several months ago. But what you really need to know is whether those controls work reliably in day-to-day operations. This is especially important during high-volume periods, staff turnover, system updates, security incidents, and tight deadlines.
SOC 2 Type II audits verify that security controls maintained their effectiveness through all these real conditions. The auditor doesn’t just check if controls exist, but rather, they evaluate if controls worked properly and as intended.
Some examples of what gets tested during the 6 to 12 month audit for SOC 2 Type II:
- Access controls: Reviewing terminated employee records and verifying system access was removed within required timeframes. Checking user access logs to confirm only authorized people accessed sensitive data.
- Security monitoring: Examining security event logs to confirm continuous monitoring happened. Verifying security incidents were detected, logged, investigated, and resolved properly.
- Change management: Reviewing system changes to verify they followed documented procedures and were tested before going live.
- Data processing: Making sample transactions to verify complete, accurate, and timely processing. Testing that data validation controls caught errors.
Questions to Ask Vendors About Their SOC 2 Compliance
- “Do you have SOC 2 Type I or Type II attestation?” Ask for specific clarification. Some vendors say “SOC 2 compliant” without mentioning which type.
- “Can you share your most recent SOC 2 report under NDA?” Legitimate vendors will provide their report under a mutual Non-Disclosure Agreement.
- “If Type II, what was the audit period?” Look for 12-month audit periods. While 6 months meets minimum requirements, 12 months is standard and provides more thorough verification.
- “If Type I, what’s your timeline for Type II attestation?” Understanding their Type II plans shows whether they’re working toward more comprehensive verification.
- “Were there any exceptions or findings in your most recent report?” Clean opinions with no exceptions show strong control effectiveness.
- “Which Trust Service Criteria does your SOC 2 cover?” Not all audits cover the same criteria. For data processing vendors, look for Security, Processing Integrity, and Confidentiality coverage.
- “Who conducts your SOC 2 audit?” Auditor quality matters. Nationally recognized CPA firms bring rigorous standards and deep SOC 2 expertise.
When SOC 2 Type I Makes Sense
Type I compliance plays an important role and shouldn’t be dismissed.
For newer vendors building their compliance programs, Type I represents significant investment and commitment. It shows they’ve invested in building a proper security framework, engaged qualified auditors, and documented policies thoroughly.
Type I works well for:
- Evaluating vendors for lower-risk, non-critical applications
- Conducting preliminary vendor assessments before deeper review
- Assessing vendors actively working toward Type II
If you’re evaluating a vendor with Type I, asking about their Type II timeline helps. Organizations typically complete Type I, run controls for 6-12 months, then pursue Type II attestation and establish ongoing annual audits.
Make Type II Your Standard for Critical Systems
Type I has its place, but Type II should be your baseline when selecting vendors for:
- Critical business systems your operations depend on
- Sensitive data including customer information, financial records, or regulated data
- High-volume processing where control failures would significantly impact your business
- Compliance-driven industries (healthcare, finance, education) with strict vendor requirements
- Long-term partnerships where sustained control effectiveness matters
Another key factor: Type II streamlines enterprise partnerships. many procurement processes specifically require it, comprehensive reports speed due diligence, and it demonstrates operational maturity that builds confidence in long-term vendor relationships.
The Tab Service Company Standard: 15+ Years of SOC 2 Type II Compliance
At Tab Service Company, we’ve maintained SOC 2 Type II for over 15 years consecutively. Before that, we maintained its predecessor audits prior to SOC 2’s introduction in 2010.
As a result, security controls are ingrained in our very operations. They don’t slip during busy seasons, they don’t get skipped under deadline pressure, and they don’t need constant oversight to maintain.
Our SOC 2 Type II includes:
- Annual audits by Plante Moran, one of the nation’s most trusted CPA firms
- Full 12-month audit periods with clean opinions and zero exceptions
- Coverage for Security, Processing Integrity, and Confidentiality
Making the Right Choice for Your Organization
When evaluating vendors who will handle your sensitive data, understanding the Type I versus Type II difference helps you make informed decisions aligned with your risk tolerance.
Type I provides valuable confirmation that controls are thoughtfully designed and the vendor has invested in building a security framework.
Type II provides comprehensive verification that controls work effectively and consistently in practice, the vendor maintains controls across varying business conditions, and the organization shows sustained operational discipline.
For critical systems and sensitive data, SOC 2 Type II is necessary. It provides the level of independent verification that supports confident partnership decisions. Type I serves as a good starting point for newer vendors. But when your organization’s data security depends on vendor controls working consistently and effectively over time, Type II is the right standard.
Partner with a Vendor That Takes Security Seriously
When you’re evaluating vendors for critical data processing, you need a partner with proven, sustained security practices, not just a recent audit.
Tab Service Company brings 15+ years of consecutive SOC 2 Type II compliance and deep expertise in secure data processing for healthcare, education, financial services, and enterprise organizations.
Learn About Our Security & Compliance | Explore Our Services | Contact Our Team